Robust and resilient network security
Most often, network security breaches are not caused by the exploitation of encryption technology weaknesses. Rather, they are mostly the result of human factors, such as not enforcing network security best practices. For example, when an organization deploys a video management system (VMS) with 300 IP cameras, the installer needs to manage around 300 IP addresses, 300 MAC addresses, and 300 login credentials for each IP device. This creates a high level of complexity to manage throughout the whole lifecycle of the system.
Most IP cameras now ask users to change the login credentials at the first login, with upper and lower case letters, numbers, and special characters. However, when you have 30 0 separate logins, installers often do one of two things: use a single login for all 300 cameras or create separate logins and record them in an Excel spreadsheet—both of which make the system very easy to breach.
The elimination of complexity and human error
IDIS has eliminated this complexity and designed its Total Solution with network security in mind. DirectIP™ utilizes true plug-and-play with the implicit pairing of devices, and in doing so, the system reduces the amount of information that needs to be managed. This is also the case for multi-site applications through our For Every Network (FEN) technology.
The registration (i.e. pairing) of IDIS IP cameras and network video recorders (NVRs) is implicit and hidden from users, like a Bluetooth headset paired with a mobile phone; once paired, the headset communicates exclusively with the paired phone.
Using this approach, IDIS ensures that installers do not have to manage the device, minimizing the level of human risk during implementation. This is a huge benefit because it can easily reduce the complexity by 30-60fold. A user only needs to manage one IP device, the NVR. At IDIS, we call this “manageable complexity.” It becomes an even more useful concept for large applications or as an organization’s system grows.
Protecting the corporate network
More and more organizations are moving away from implementing IP video surveillance on their corporate network due to security concerns and the rise in data theft. The IDIS Total Solution uses a dedicated IP camera subnet, separate from a customer’s corporate network, separating the video traffic and making it very difficult to establish an unauthorized connection into a corporate network.
At IDIS, we educate our installers and integration partners to design a physically separate network, or to configure a dedicated network by VLAN, and move end users away from wanting to use their existing corporate network.
Proprietary technology
IDIS devices, such as NVRs, use a proprietary embedded Linux (i.e. not off-the-shelf) that only authorized network modules can run, and IDIS does not allow any third-party apps to run inside the IP camera. Since IDIS leverages proprietary protocols, this makes them very difficult to exploit. IDIS has also developed proprietary file structures whereas some manufacturers use Windows or off-the-shelf Linux, another example of IDIS hardening network resilience. Even a common network module, such as our HTTP/HTTPS server, is a proprietary implementation, which will make many known attacks ineffective. IDIS also uses industry-standard SSL/TLS when communicating across a network as well as the encryption of login details, IP filtering, IEEE 801.1x, and TLS/SMTP.
Often times, there are concerns that manufacturers can access an end user’s system. With IDIS, technology users’ passwords are encrypted. For example, if an administrator account password for an NVR is lost, then there is no way to reset it, even by IDIS engineers who designed the system. Unlike other manufacturers, IDIS does not use “backdoors.” These “backdoors” are typically used to gain access and provide remote customer support, but at the same time, they can spur fears of spying and espionage. There are recovery options with IDIS systems, but these need to be set up by the installer when the system is implemented. So, for the sake of network security, IDIS cannot access any of its own installed systems.
Data integrity
IDIS has developed the cornerstone of our offerings to ensure data integrity and combat the risk of damaged hard drives. These core technologies were developed to ensure the usability, reliability, integrity, and safety of our customers’ footage data.
Reliable video evidence
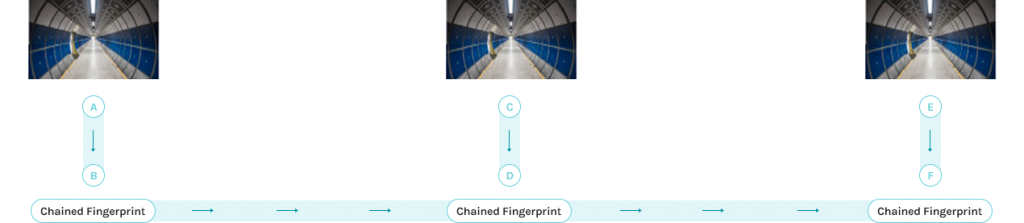
IDIS uses a proprietary integrity check algorithm called IDIS Chained Fingerprint. Every single neighbouring image is chained with a fingerprint value. This chained fingerprint value is stored along with the images, so whenever the stored images are exported, if this chain is broken, it signifies that there was a possible tampering of the images. This is incredibly important in terms of evidence since video footage is often dismissed from courts because tampering cannot be ruled out. In addition, IDIS video streams are protected by Secure Sockets Layer (SSL) cryptographic protocols when communicating across a network, making them incredibly difficult to tamper with or alter.
Built-In Resilience
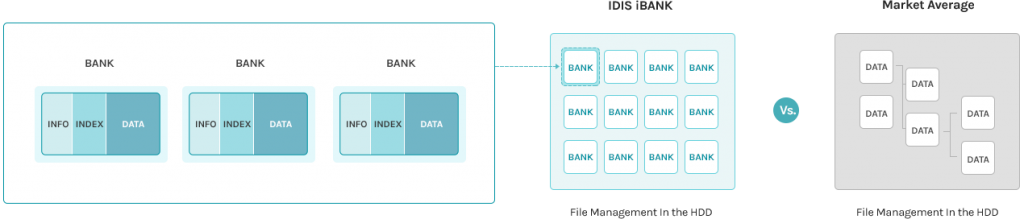
IDIS also uses a proprietary and patent-protected database file system, IDIS iBank. This purpose-built file system provides every IDIS NVR and external eSATA storage device with high-performance playback and stable use of HDD disk drives. IDIS iBank automatically restores and restructures damaged index info within the HDD disk drives, making it possible for IDIS NVRs and external storage to run properly, even in extreme cases of damage, providing the stability and reliability for even the most mission-critical of surveillance operations.
